My daughter and I went to see “Inside Out 2,” and as I watched, I could truly relate as I’m in the last few years of raising my two teenagers. I must say that having anxiety and embarrassment join the cast of emotions in the sequel was a delight to watch!
After the movie, I started to reflect and saw many parallels between the emotional rollercoaster of the Disney teenager trying to keep her cool and the day-to-day experiences of cybersecurity leaders and their teams. Especially when it comes to securing access for human and machine identities across cloud environments, adhering to compliance requirements, and meeting the business demands of convenience and time to market.
When tackling an identity security challenge or project, emotions can run high. Let’s dive in!
5 Key Emotions Cybersecurity Leaders May Be Feeling Right Now
Here are a few emotions that are trending on the high side for those on the frontlines of identity security that we speak with every day.
Overwhelm
Cybersecurity and IAM teams are charged with protecting their organizations with stretched resources while shouldering the burden of potential reputational damage, customer risk, and failed audits. Working under the constant and growing threat of cyberattacks is enough to wear out the strongest of adrenals. A recent study found that 74% of cybersecurity professionals globally say that they have taken time off due to work-related mental well-being problems.
Add to that, the pressures of staying continuously compliant keep teams busy reviewing access privileges and proving controls are adequate. Manual access reviews, lack of unified visibility across the cloud and SaaS for all identities (human and non-human), and the rubber-stamping of overprivileged and dormant accounts can lead to increased risk, stalled decision making, and counterproductivity. The sheer volume of cybersecurity pressures and tasks can lead to a debilitating sense of overwhelm.
Fear
This emotion may not be as obvious on the surface, but fear of the unknown can keep many CISOs up at night. “What access issues am I missing that could wreak the most havoc? How would I know? Where are my greatest non-human identity risks? How can I protect the organization from AI-infused attacks?”
You can’t protect what you can’t see.
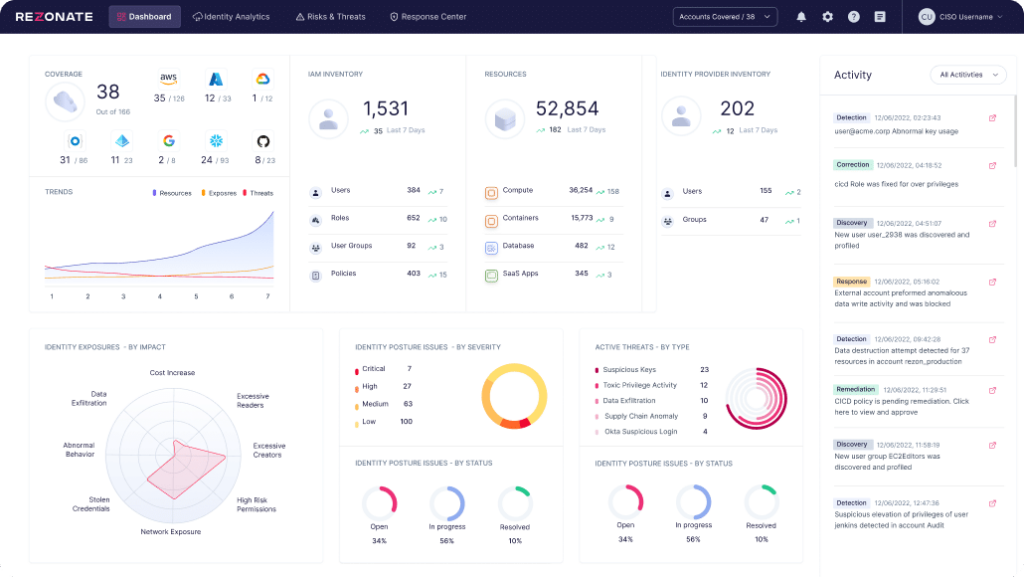
Many cybersecurity teams struggle to get end-to-end visibility into access privileges, risks, and activities for hundreds and thousands of human and non-human identities accessing their cloud and critical SaaS applications. Disparate systems and teams lead to a lack of visibility across silos allowing blind spots which can be exploited by malicious actors, making it a daunting task to secure every corner of the digital landscape.
Establishing a real-time, unified view across every user, their privileges, security controls, behavior, and risk levels provides a contextual layer of understanding to access and areas of high risk. This visibility enables better actionability supported by better decision making and results in faster time to detection and response when risk is elevated or threats are present.
Anxiety
Fear isn’t always bad – it signals that we need to prepare and look at something a little closer. That’s where anxiety can jump in and motivate cybersecurity teams to prepare for challenges proactively.
Some security leaders may feel anxious. After all, they feel a huge personal responsibility for securing their organization. The board and customers are counting on them. As with the Joe Sullivan case, the former CISO of Uber. Sullivan was sentenced to three years of probation and underwent a grueling legal battle when Uber was breached in 2016. His case has caused anxiety among cybersecurity professionals, spurring fears that they could face legal penalties for simply doing their jobs. In October 2023, Timothy Brown, SolarWinds CISO was charged with fraud and internal control failures. The SEC says that Brown was aware of SolarWinds’ cybersecurity risks and vulnerabilities but failed to resolve the issues or, at times, sufficiently raise them further within the company.
And when it comes to resolving issues, we see SecOps and IAM teams experiencing remediation anxiety when they need to respond to a threat in real time. This goes back to the visibility and real-time actionability support lacking for most cyber teams right now. It’s hard to understand the impact of removing an identity’s access. Some may hesitate to block or remediate access for an impacted identity, worried that such actions might inadvertently disrupt business operations or customer experiences. But, inaction can also lead to big trouble.
This anxiety stems from the delicate balance between maintaining security and ensuring seamless business continuity. The fear of causing more harm than good can paralyze decision-making, leaving vulnerabilities unaddressed.
CISOs and their teams need visibility with real-time risk insights and actionable identity-centric security that’s able to support them while they navigate all of these challenges.
Stress
The constant vigilance required to respond to identity-based attacks leads to what is being reported now as increased cases of burnout. In fact, a recent study confirmed that 80% of CISOs classified themselves as “highly stressed,” CISOs and their teams find themselves in a perpetual state of alert, struggling to identify the root cause of breaches and secure all access points. The relentless pressure of the job is compounded by the expectations of regulators, boards, and shareholders who demand unwavering protection of sensitive data and resources. The 24/7 nature of cybersecurity takes a toll, leading to exhaustion and diminishing effectiveness over time. It’s enough for any human to feel like they’re fighting a losing battle.
With the proper support, tools, and partners, CISOs and their teams can turn this around and make use of the newer approaches of innovative identity-centric security tools, like Rezonate, to make life easier and help them to be more successful each day at outpacing attackers.
Despair
When faced with the reality that you’ve still got blind spots, even with all the time and money invested in existing security and identity and access management tools, cybersecurity teams (and possibly leaders) could be tempted to throw in the towel. Or, fall prey to paralysis or pessimism.
Taking a conservative “wait and see” approach with the legacy IAM or IGA products may simply perpetuate your issues. Attackers are evolving at a rapid pace, especially now with the power of AI. Using stolen credentials to slip past defenses and lurk undetected within networks for weeks or months. Acknowledging the limitations of existing security solutions and processes can help you to find a better way.
Act Now for Joy and Peace of Mind
By acknowledging your feelings (and those of your team members), you can understand where the greatest challenges lie. But first, we must acknowledge how much the world has changed, and what needs to be done differently:
- Unified end-to-end view across cloud, SaaS, and IdPs including context, risk, and privilege insights
- Proactive posture management with real-time threat detection and response
- Coverage for both human and non-human identity in one platform
It’s time for a new approach to identity security, one that’s holistic, intelligent, and fast-acting.
With a new approach and trying an identity-centric security solution, you can go from a state of constant stress and reaction to one of proactive, confident identity security.
Rezonate Offers a Pathway to Success
Our identity-centric security platform enables organizations to transform overwhelm, fear, and anxiety into confidence, and turn stress and despair into clarity and control.
Here’s how to start feeling better when it comes to identity security:
- Get clarity: Gain unparalleled visibility into identities accessing your cloud, SaaS, and identity providers.
- Know your risks: Quickly identify your greatest risks and make informed decisions to automate remediation tasks.
- Bridge the gaps: Leverage the full support of IT, Security, GRC, and DevOps. Everyone can leverage the platform to manage identities and access in their respective areas.
- Move quickly: With better visibility at your fingertips along with real-time alerts, dashboards, and reports, you’ll see exactly where you’re at risk and understand how to swiftly respond with precision.
- Automate and streamline: Automated and guided remediations help to ensure continuous compliance while proactively securing your identity attack surface
Whether you are experiencing one or all of the emotions we’ve discussed, let us help you achieve a more positive day-to-day vibe. Rezonate is ready to be your partner in identity security transforming the emotional burden of it all into a manageable and rewarding endeavor. Schedule a call to discuss your current challenge today!