23 Oct

Top Identity Threat Exposures You Need to Address Now
Cloud environment intrusions have increased by 75% year on year, and it takes around 120 days for organizations to detect cyberattacks in the cloud. Additionally, the rise of remote working has only intensified the complexity. With employees connecting from various
15 Oct

100 Breakthrough Prompts for Your Best User Access Review
User access reviews are vital for maintaining robust identity security and ensuring compliance across your cloud and SaaS environments. With the growing complexity of managing identities—both human and machine—security teams must continuously monitor and validate access to minimize risks like
01 Oct
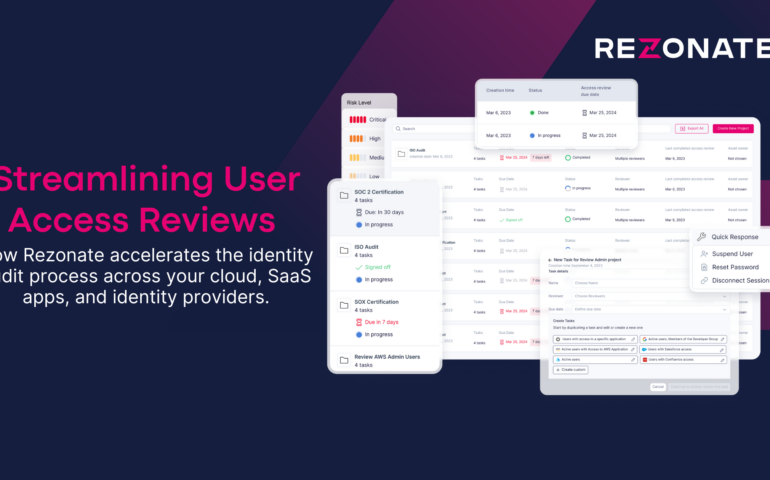
How to Unburden Your SaaS and Cloud Access Reviews
Managing access to cloud and SaaS applications is essential for securing critical business operations. Access reviews are a vital component of this process. They ensure employees have the appropriate permissions to do their jobs without exposing your organization to unnecessary
30 Sep

Your Pre-2025 User Access Review Plan: How to Ace Your Audits and Boost Security
This is your quick guide to conducting a water-tight user access review, passing your end-of-year IAM audits, and safeguarding your organization from identity threats before 2025 comes around. With the year drawing to a close, it’s the perfect time to
05 Sep

Win the Identity Security Battle: Keep Your Crucial Assets Safe
As you move beyond the safe and controllable traditional network walls and embrace a cloud-centric environment with more and more SaaS applications serving a hybrid working environment, you’ll discover that your users and machines have been given unprecedented levels of
10 Jul

Inside Out, Identity Security Edition
My daughter and I went to see “Inside Out 2,” and as I watched, I could truly relate as I’m in the last few years of raising my two teenagers. I must say that having anxiety and embarrassment join the

