24 Oct

Okta Threat Hunting: Auditing Okta Logs Part 2
Update Note Due to the recent events at MGM, which included the compromise of MGM’s Okta tenant, and the surge in attacks of Okta Admins, we have updated the threat-hunting article, adding a few relevant queries to increase visibility surrounding
04 Oct

Defending Azure Active Directory (Entra ID): Unveiling Threats through Hunting Techniques
Azure Active Directory (Entra ID) stands as one of the most popular and widely-used cloud-based identity and access management services provided by Microsoft. It serves as a comprehensive solution for managing user identities and controlling access to a diverse range
19 May

Threat-Hunting for Identity Threats in Snowflake
The Snowflake platform has revolutionized how organizations store, process, and analyze large volumes of data. It offers a fully-managed data warehouse-as-a-service solution, providing a scalable and flexible architecture allowing seamless data integration from multiple sources. As Snowflake rises in popularity
17 Jul

Okta Logs Decoded: Unveiling Identity Threats Through Threat Hunting
In the ever-evolving world of cybersecurity, staying steps ahead of potential threats is paramount. With identity becoming a key for an organization’s security program, we increasingly rely on Identity providers (IdP) like Okta for identity and access management, and for
16 May
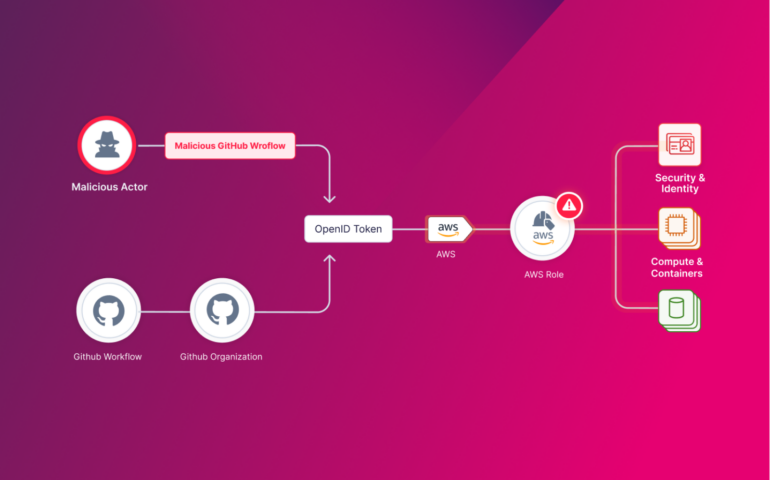
From GitHub to Account Takeover: Misconfigured Actions Place GCP & AWS Accounts at Risk
In April 2023, Rezonate research team explored prevalent misconfigurations of GitHub integration with cloud native vendors. GitHub OIDC-based trust relations have been found with the critical misconfigurations that leave connected AWS/GCP accounts vulnerable to potential takeover attacks. Although this issue
27 Feb

CircleCI Breach: Detect and Mitigate to Assure Readiness
On January 4, 2023, CircleCI, a continuous integration (CI/CD) and delivery service, reported a data breach. The company urged its customers to take immediate action while a complete investigation is ongoing. First critical actions recommended by CircleCI were to ‘rotate

